         |
Strategic Planning Document -
National Security
3. Implementation
a. The National Security Implementation Environment
(1.) Policy Imperatives
Two important policy imperatives impacting our national
security science and technology policy are:
Breaking down barriers between military and civilian sectors of the technology and industrial base. The
Administration is taking new approaches designed to enhance "spin-on" mechanisms which allow the government to derive maximum
benefit from advances in the commercial sector. The fundamental means for carrying out this new approach is cost-sharing
partnerships between government and industry. All federal Research & Development agencies (including the nation's
federal laboratories) are to act as partners with industry wherever possible. With partnerships, federal investments can be
managed to the mutual benefit of both government and business. Partnerships can also ease the process of technology transfer
between civilian and military sectors. Development of dual use technologies, processes, and products, to include the vital
supporting technology and manufacturing infrastructure becomes a priority for national security science and technology. Not only
does dual use development make good economic sense for the nation, it is a critical element in the drive to satisfy our
military requirements at less expense. Ongoing acquisition reform initiatives are key to this policy imperative.
Balancing international cooperation with maintenance of
U.S. technological advantage. With some exceptions, the U.S.
has maintained a lead or parity in most advanced technology and
manufacturing capabilities. In areas where we are not the
leader, or where we can benefit from combining efforts, resources
and talent, international cooperation provides a means to
leverage foreign technologies. Cooperation, however, comes with
the potential risk that we will find ourselves on a future
battlefield opposed by a force with some equivalent technological
capability. To balance international cooperation and technology
transfer with the maintenance of technological superiority in
those areas that are critical to our national and economic
security, we must analyze the benefits and risks associated with
each cooperation and transfer agreement.
(2.) Current and Emerging Societal Issues impacting the
National Security Science and Technology Program
Science and technology investments both influence and are
influenced by our values and priorities as a society. Many
societal issues impact our national security science and
technology program, including:
Competing National Interests. Multiple national
priorities compete for limited resources.
Characterizing the Threat. Society's understanding of
the significant threats to U.S. interests affects investment
priorities.
Minimize Casualties and Damage. To minimize combatant
and non-combatant casualties and collateral damage during
military operations, the national security community has placed
increased emphasis on science and technology programs that
improve capabilities to identify friend from foe, enhance
conflict prevention, provide non-lethal options, and produce high
precision weapons.
Responsible Environmental Management. Science and
technology investments must be made in the context of responsible
stewardship and sustainment of natural resources and the
environment. When making national security science and
technology investments, we must consider all aspects of
environmental management, including restoration, compliance with
regulations, and stewardship.
Responsible Energy Management. U.S. national security
requires access to efficient energy sources with minimum
dependency upon unreliable foreign suppliers. Developing
alternate energy sources has increased in importance.
(3.) External Input
The many federal agencies and departments each employ private
sector advice in implementing the national security science and
technology strategy. Private sector input to the national
security science and technology agenda is drawn from a rich
variety of sources and mechanisms. Formal mechanisms operate at
the Presidential level, at the interagency level, and within
federal agencies and departments. These mechanisms include
commissioned panels and advisory boards, government participation
in public symposia, interface with industry, and special
studies.
These federal/private collaborations support the
Administration's goals to serve commercial and defense
technologies in parallel, and to the maximum extent practical,
integrate the national security and commercial industrial bases.
These merging industrial enterprises will be capable of
developing and building more affordable products and enhancing US
industrial economic competitiveness in global marketplace.
(4.) International Dimension
The technical agencies of the U.S. government also engage in a
wide range of bilateral and multilateral international scientific
programs that support their missions. International science and
technology programs within the national security area can be
classified into the following broad categories:
- Collaborative science and technology programs with other
countries in support of agency missions.
- The New Independent States -- Industrial Partnering Program
(NIS-IPP) that is conducted by Department of Energy in
consultation with Department of State to redirect the expertise
of scientists and engineers of the former Soviet Union from
weapons-related activities to non-military applications of
commercial value and mutual benefit.
- Monitoring, reporting and information exchange activities
aimed at identifying and exploiting technologies developed in
other countries to avoid technological surprise.
- Programs aimed at fostering stability by helping to address
problems which are global in scope, such as excessive population
growth, food scarcity, environmental degradation, and
deteriorating health conditions.
The Committee on International Science, Engineering and
Technology (CISET) of the National Science and Technology Council
addresses issues in international scientific cooperation and
issues that lie at the intersection of US foreign policy and the
nation's research and development agenda. The CISET Strategic
Implementation Plan articulates the goals and methods of that
Committee and further elaborates on the international dimension
of national security science and technology.
b. Areas of Focus
(1.) Introduction
Support Our National Military Strategy . The
fundamental mission of national security science and technology
is to support the ability of U.S. military forces to carry out
our national military strategy. The National Military Strategy
addresses the main dangers which threaten U.S. security
interests, identifies national military objectives, determines
the military tasks the military must accomplish to achieve these
objectives, and examines the capabilities and forces required.
The objective of national security science and technology is to
develop and transition options for affordable, decisive military
capability based on superior technology. The science and
technology investments strive to: maintain technological
superiority of US forces; provide the basis for new capabilities
and new missions such as regional conflicts and countering the
proliferation of weapons of mass destruction; enable force
drawdown without loss in operational capability; develop the
technological basis for force multipliers for use by smaller
forces; achieve higher readiness through more efficient execution
of training and ensuring an adequate science and technology
infrastructure that capitalizes on technology innovation.
Highest priority is placed on science and technology
investments that help maintain technological superiority in joint
warfighting capabilities. The Joint Staff and JROC identified
five future joint warfighting capabilities most needed by the
U.S. Combatant Commands. Those needs, coupled with technological
opportunity, guide national security science and technology
investment decisions.
In the changing world order and given the broad implications
of national security, the National Science and Technology Council
has identified three other significant areas of focus for
national security science and technology. These areas are
intertwined with overlapping boundaries:
Science and Technology Applications to Post-Cold War
Missions. In addition to supporting our core capability to
win two nearly simultaneous major regional military operations,
our national security technology investment needs to be
applicable to military missions at the lower end of the
operational spectrum that are growing in importance in the
post-Cold War world.
Building International Stability and Preventing
Conflict. We need to give increasing attention to our ability
to prevent conflict before it requires the engagement of U.S.
military forces. Science and technology cooperation plays an
important role in this area.
Weapons of Mass Destruction. Technology plays a central
role in efforts to ensure that we prevent the reemergence of the
nuclear threat, counter the proliferation of weapons of mass
destruction and the means of their delivery, verify and monitor
existing and new arms control agreements, and ensure the
effectiveness of the smaller U.S. nuclear research and production
capability.
The areas of focus are described in detail in section b.(3.)
below.
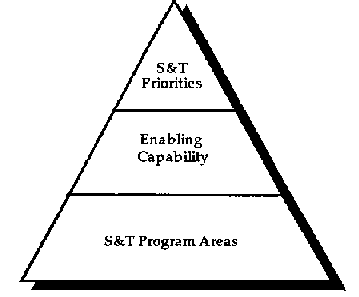
(2.) Priority Mapping Methodology
The Committee for National Security identified science and
technology priorities for each area of focus. Enabling
capabilities needed to accomplish these priorities were then
enumerated. Finally, the supporting technologies required to
achieve the enabling capabilities were aggregated into Science
and Technology Program Areas. See Figure 1. (Table A-1 in
Appendix A depicts a summary representation of sample Supporting
Technologies reviewed in Science and Technology Program
Areas.)
Figure 1.
(3.) Focus Area Priorities and Enabling Capabilities
Support Our National Military Strategy. The National
Military Strategy derives its overarching guidance from the
President's National Security Strategy and is articulated by the
Joint Chiefs of Staff. Table 1 summarizes the vital warfighting
capabilities and enabling capabilities needed for national
security.
The Department of Defense designated the following as high
priority science and technology efforts in the Defense Technology
Strategy, September 1994:
- Information science and technology enables better
performance of current platforms, weapons, sensors, and people.
Information technologies are the basis for continual improvements
in communications; intelligence gathering; analysis and
distribution; battlefield situational awareness; command and
control and sensor data processing.
- Modeling and simulation holds the promise of broad
applicability; the benefits are both cost reduction and new
capability. This technology provides a fast, effective, and
inexpensive means to prepare individuals and units for possible
encounters or conflicts. Modeling and simulation can be applied
to more than just training. It can be used during concept
formulations to expand the range of technical, operational, and
system alternatives evaluated. Simulations can be the basis for
planning and decision aids to stretch the ability of commanders
to train, to plan, and to employ their forces.
- Sensors provide data about objects or physical
phenomena of importance on the battlefield. To know, to know
more, and to know it sooner than the enemy is a decisive
advantage. The sensor technology program is broadly based; it
exploits the full range of the electromagnetic spectrum. It will
improve situational awareness, target acquisition, target
identification and discrimination, and targeting.
Table 1. Enabling Capabilities for Supporting National Military Strategy
Maintain near perfect, real-time knowledge of the enemy and
communicate that to all forces in near-real time:
- Surveillance
- Improved sensor resolution, dynamic range, and all-weather
performance
- UAV endurance, stealth and affordability
- Assured, reliable identification of friend, foes and neutrals
- Information management and communications
- Interconnection of large numbers of diverse networks
- Rapid reconfigurability of information systems
- Information and information systems protection
- Heterogeneous, distributed databases
- Information management to match data to users
- Secure, reliable wideband communications
Engage regional forces promptly in decisive combat, on a
global basis:
- Improved airlift and lighter forces
- Assured, rapid neutralization of mines
- Precision strike
- Surveillance
- Autonomous guidance and control
- Enhanced lethality, particularly against buried and hardened targets
- Deployable sensors
- UAV
- Remotely emplaced, unmanned sensors
- Low observable aircraft technology (manned and unmanned)
- Standoff, precision munitions
Employ capabilities suitable to lower end of operational
spectrum that allow achievement of objectives with minimum
casualties and collateral damage:
- Improved intelligence and targeting
- Near real time knowledge of the battle environment
- Enhanced special operations capabilities
- Clandestine infiltration
- Comprehensive local surveillance
- Tailored weapons (disable, disorient, confuse, neutralize temporarily)
- Enhancement and protection of small units and individuals
- Body armor
- Counters to lasers, microwave weapons and NBC threats
- Prompt medical trauma care and prevention of unique infectious diseases
Control the use of space:
- Maintenance of uninterrupted access to information in space
- Hardening/shielding
- Communications agility
- Electronic counter-countermeasures techniques
- Precision sensing for identification of space objects
Counter the threat to CONUS and deployed forces of weapons of
mass destruction and ballistic and cruise missiles:
- Counters to aircraft, ballistic and cruise missiles, and standoff weapons
- Effective lethal mechanisms against chemical and biological threats
- Intercept capability in boost phase
- Hard underground target defeat with low collateral effects
- Underground structures detection and characterization
- Enhance collection and analysis of intelligence
- Detection and tracking of shipments and control and accountability for stocks of WMD-related materials and
personnel
- Real time detection and characterization of CW/BW agents including stand-off capability
- Passive defense capabilities enabling military operations to continue in contaminated conditions-actual or threatened (low
cost, lightweight)
- Rapid production of protective BW vaccines
- Detect and intercept low flying/stealthy aircraft and cruise missiles
- Prompt mobile target kill
Science and Technology Applications to New Post-Cold War
Missions. These mission areas are receiving special emphasis
yet are derived from the broader national military strategy.
Science and technology applications to new post-Cold War missions
place special demands upon the national security strategy. There
are four science and technology priority applications in this
area of focus:
- The Individual Warrior. The complexity of the post
Cold War situation has increased the potential need for several,
simultaneous, rapid response operations that will require superb
performance from each member of the armed forces. Post-Cold War
operations frequently preclude using large force structures.
Therefore, science and technology programs that enhance the
ability of the individual warrior (or small numbers of warriors)
have especially high value. Examples include technologies that
enhance situational awareness, individual performance, and those
that protect personnel in hazardous environments.
- Urban Environments. These new missions are often
conducted in urban environments. Crowd element identification
(friend, foe or neutral) and crowd control technologies are
particularly important. Supporting technologies include programs
such as persistent obscurants for urban terrain, high quantity
sticky foams for closing urban passageways, and acoustic and
electromagnetic weapons.
- Information Management. This technology is
particularly important to new post-Cold War operations. These
missions often require highly specialized knowledge of
individuals, decision-making systems, and local or geographical
knowledge as well as locality-based data.
- Remote Sensors. This is an especially pertinent
specific agglomeration of the application of the above three
priority applications, and thus has a unique levering capability
for the new world. The ability to covertly place and link remote
sensors and to detect movement and classify objects in accordance
with their unique signatures greatly enhance operations in new
post-Cold War missions. Autonomous sensors can form an
undetectable electronic network capable of relaying intelligence
that enhances abilities in many ways, including precision
targeting in real-time.
There are nine broad categories of enabling capability
important to carrying out new post-Cold War missions. These
enabling capabilities are listed in Table 2.
- Table 2. Enabling Capabilities for Science and technology
Applications to Post-Cold War Missions*
- Mobile Forces
Mission Planning
Improved training
Preventive Diplomacy
Intelligence Collection and Analysis
Conflict Resolution/Crisis Response
Offensive and Defensive Capabilities, including Surveillance
Global and Theater Command, Control, and Communication
Mobility Support (Including Logistics and Maintenance Support)
*Not listed in order of importance.
Building International Stability and Preventing
Conflict. The strength of our military forces and the
resolve to use them when necessary have a deterrent effect on
those who might be tempted to challenge our interests. As an
integral part of our national security strategy, science and
technology contribute to promoting economic security, democracy,
and sustainable development around the world. Certain
capabilities that are primarily "warfighting" capabilities are
also key to success in restoring stability or deterring
conflict.
The following science and technology priorities apply to this
focus area:
- Intelligence and Surveillance. This priority area
requires real-time, day/night, all weather intelligence
gathering, embargo compliance monitoring technology, refugee
movement monitoring technology, remotely installed sensors, and
lightweight, mobile information gathering systems. (Note:
federal science and technology investments for intelligence
gathering for peace operations are captured under Science and
Technology Applications to Post-Cold War Missions.)
- Detection of Weapons of Mass Destruction. This
priority area requires technology to help locate and identify
weapons of mass destruction systems and their sub-elements,
portable detection systems, detection of nuclear, chemical and
biological materials while on the move, and near-real-time data
transmission. (Note: federal science and technology investments
involving weapons of mass destruction are captured under Weapons
of Mass Destruction.)
- Modeling, Simulation and Predictive Data Bases. This
priority area requires technology to help provide advance warning
of humanitarian crisis and predict the location and possible
intensity of crisis, force and support tracking systems,
information dissemination to forces and support systems, and
access to real time data.
- Non-Lethal Weapons. This priority area requires
technology to help control crowds, disable or disrupt military
logistics with minimum casualties, disrupt or disable
communications, transportation and utilities, and destroy or
disable conventional weapons and mass destruction weapons.
- Mine Detection and Neutralization. This priority area
requires technology to provide rapid, accurate mine detection and
effective mine elimination equipment, especially for land mines
and unexploded ordnance.
- Water Supply and Purification. This priority area
requires technology that can support water delivery from remote
points of origin, portable water purification systems for central
source (10,000 to 100,000 persons) or individual use, and
purification kits for untrained or non-literate individuals.
- Food Distribution and Preservation. This priority
area requires technology to support food delivery from remote
points of origin, secure methods of food delivery (for both
recipients and food deliverers), regional food stockpiling, and
transportation assets.
- Waste Management. This priority area requires
technology to support waste management and water supply
protection during mass migrations, civilian supply
pre-identification and stockpiling, epidemiological-chemical
products and infrastructure equipment (supporting between 10,000
and 100,000 persons), and waste treatment kits for use by
untrained, non-literate individuals.
The Committee on International Science, Engineering, and
Technology is examining a series of science and technology
efforts which can contribute to building stability and preventing
conflict, including science and technology related to population
growth, food and nutrition, infectious diseases, and others to be
identified in the future.
The enabling capabilities important to achieving the science
and technology priorities in this area of focus are listed in
Table 3.
- Table 3: Enabling Capabilities for Building International
Stability and Preventing Conflict*
- Control crowds
Access to real time data
Regional food stockpiling
Remotely installed sensors
Portable detection systems
Refugee movement monitoring
Rapid, accurate mine detection
Embargo compliance monitoring
Near-real-time data transmission
Force and support tracking systems
Advance warning of humanitarian crisis
Waste management during mass migrations
Prediction of location and intensity of crisis
Water supply protection during mass migrations
Civilian supply pre-identification and stockpiling
Lightweight, mobile information gathering systems
Food and water delivery from remote points of origin
Real-time, day/night, all weather intelligence gathering
Information dissemination to forces and support systems
Neutralization of combatants mixed with non-combatants
Disruption or disabling of communications, transportation, and utilities
Secure methods of food delivery (for both recipients and food deliverers)
Water supply and purification kits for untrained or nonliterate individuals
Waste treatment kits for use by untrained, non-literate individuals
Effective mine removal equipment (land mines and unexploded ordnance)
Destruction or disabling of conventional weapons and weapons of mass destruction
Portable water purification systems, central source or individual use (10,000 to 100,000 persons)
Disabling or disruption of military logistics with minimum casualties
Detection of nuclear, chemical and biological materials moving across borders, airports and seaports
Location and identification of weapons of mass destruction systems and their sub-elements
Epidemiological-chemical products and infrastructure equipment (10,000 to 100,000 persons)
*Not listed in order of importance.
Weapons of Mass Destruction. The President has
identified countering the proliferation of weapons of mass
destruction and their delivery systems as one of the most urgent
priorities facing the nation. At least twenty countries -- many
hostile to the United States and its allies -- have now or are
seeking to develop the capability to produce nuclear, biological
and/or chemical weapons of mass destruction and the means to
deliver them. The Committee for National Security has identified
the following science and technology priority areas for this area
of focus.
- Nonproliferation, Arms Control and Disarmament. Our
arms control, nonproliferation, and counterproliferation programs
are a critical component of our strategy to limit the spread of
nuclear, chemical and biological weapons by: reducing incentives;
enhancing predictability; reducing fear of aggressive intent;
reducing the size of national defense industries establishments
and permitting the growth of nonmilitary industries; ensuring
confidence in compliance through effective monitoring and
verification; and ultimately contributing to a more stable and
calculable balance of power.
- Detection, Monitoring and Verification. While it is
critical that we have the ability to detect proliferant
activities and to monitor, verify and implement international
regimes and agreements which seek to prevent the proliferation of
nuclear, chemical, biological and other advanced weapons, it is
equally important that we also have technologies that provide
adequate warning and indications of threats to U. S. national
security, identify opportunities for advancing our interests and
facilitate the direction of new efforts against proliferation of
weapons of mass destruction.
- Nuclear Stockpile Stewardship. With the current
moratorium on underground nuclear testing, and intensive
negotiations in progress on a verifiable Comprehensive Test Ban
Treaty, we must also ensure the safety, security, and reliability
of the nuclear stockpile and competence of our core scientific
personnel. These programs are fundamental to the retention of
nuclear forces sufficient to deter any future hostile foreign
leadership with access to nuclear forces. The unique role of the
DoE in Nuclear Stockpile Stewardship entails maintaining and
enhancing the fundamental scientific and technological
understanding of nuclear weapons needed to predict, evaluate, and
ensure the safety and reliability of the enduring nuclear
stockpile without underground nuclear tests. This further
requires enhanced experimental capabilities to support essential
nuclear weapons testing without underground tests, improved
computational simulations and predictive capabilities for nuclear
weapons, advanced technologies for producing essential nuclear
weapon materials, and development of the Factory of the Future
for intermittent manufacturing of nuclear weapons components.
Most important, it is also absolutely necessary to stabilize and
sustain the full range of core scientific and advanced
technological competencies (experts and facilities) required to
maintain the safety and reliability of the stockpile and evaluate
it from month to month and year to year.
Implementation
(continued)
President and First Lady | Vice President and Mrs. Gore
Record of Progress | The Briefing Room
Gateway to Government | Contacting the White House
White House for Kids | White House History
White House Tours | Help | Text Only Privacy Statement | |